Record-High Activity in Ethereum Network Caused by Address Poisoning Attacks
- Over $740K already stolen, and this number will keep growing
- This became possible thanks to the Fusaka upgrade, which made spam transactions cheap enough to be profitable
- This attack is ongoing right now
The number of new addresses grew 2.7 times compared to the average 2025 level. The peak week of January 12 showed 2.7 million new addresses—170% higher than typical values.
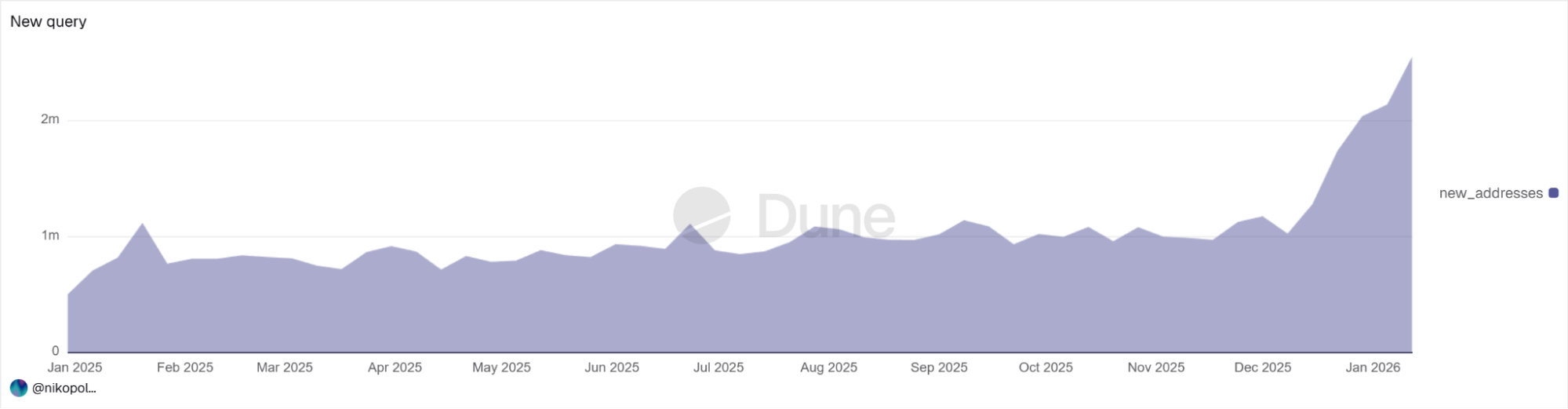
Sharp increase in new Ethereum addresses
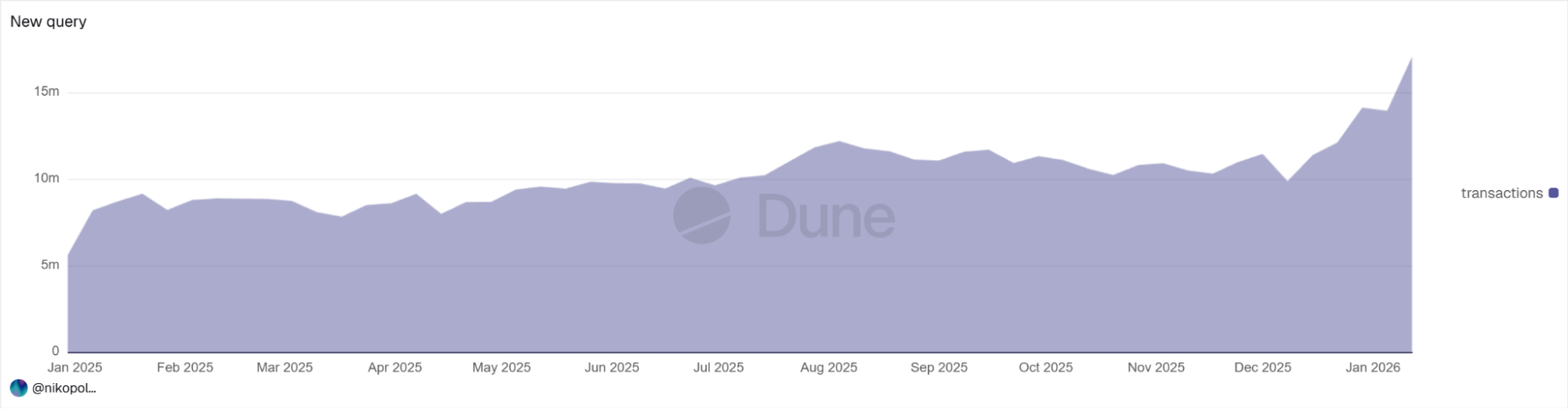
The number of transactions on Ethereum network grew 63% from 10.5M per week to a record 17.1M.
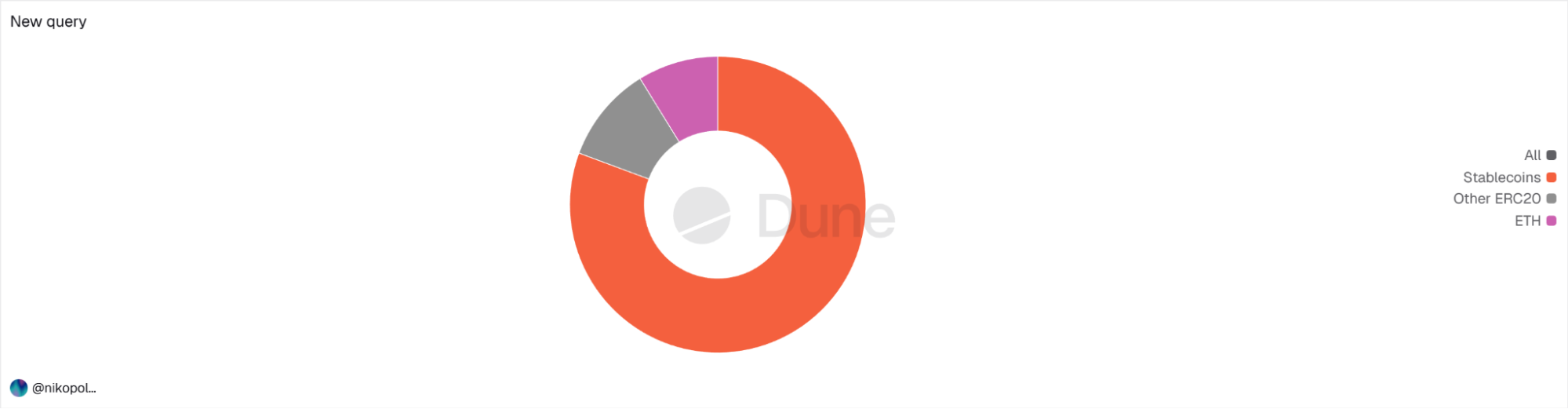
I wanted to find what caused the increase in addresses, and it turned out this unusual growth is 80% driven by stablecoins.
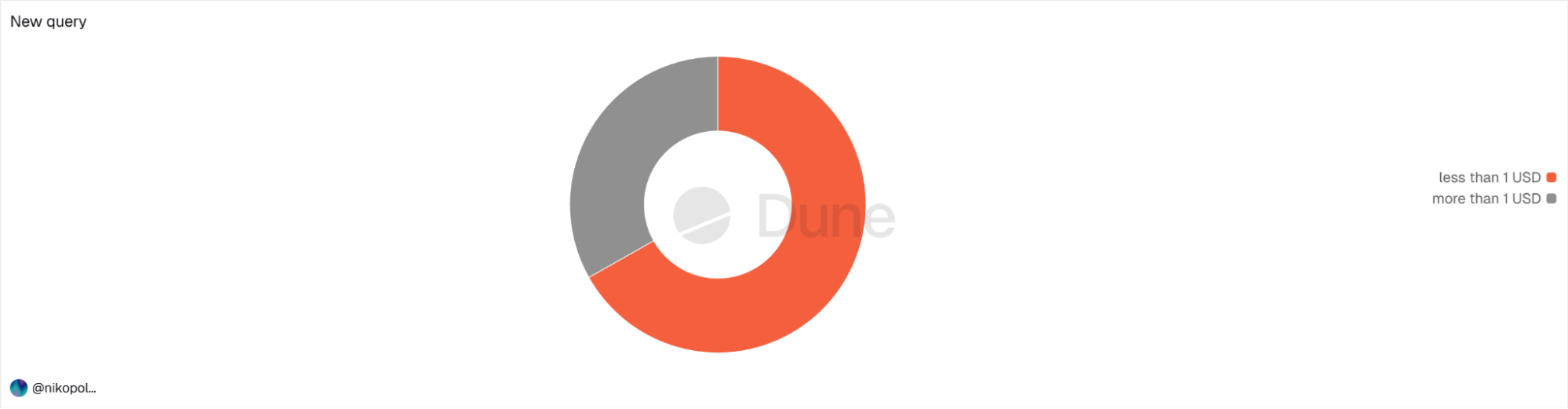
After that, I needed to understand the nature of stablecoin transactions. I calculated how many users received less than a dollar as their first stablecoin transaction, and it turned out 67% of addresses fit this pattern. 3.86M out of 5.78M addresses received dust as their first transaction.
To identify dust distributor addresses, I filtered all USDT/USDC senders of transfers <$1 for the period December 15, 2025 - January 18, 2026, counted unique recipients for each, and filtered those who sent to at least 10,000 addresses.
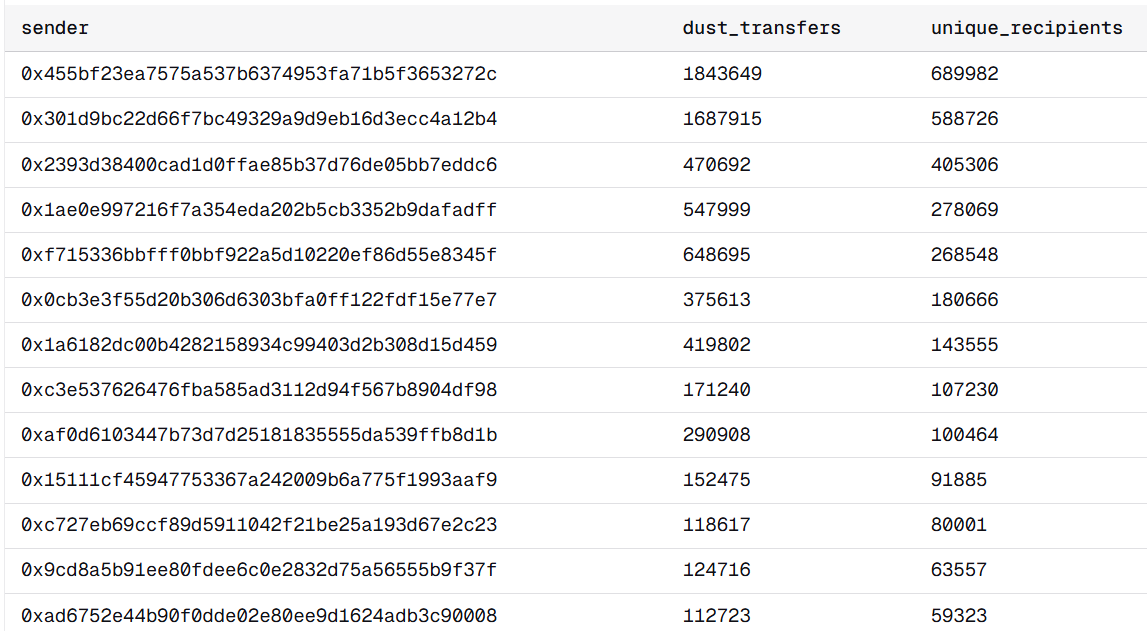
Top contract addresses distributing dust to bait addresses
Here are the top-3 dust distributors:
0x301d9bc22d66f7bc49329a9d9eb16d3ecc4a12b4 - sent to 589K
0x2393d38400cad1d0ffae85b37d76de05bb7eddc6 - sent to 405K
These are smart contracts that automate mass distribution of poisoning dust.
The source code of one such contract has a fundPoisoners function that finances hundreds of poisoning addresses in a single transaction, sending each dust tokens and some ETH for gas.
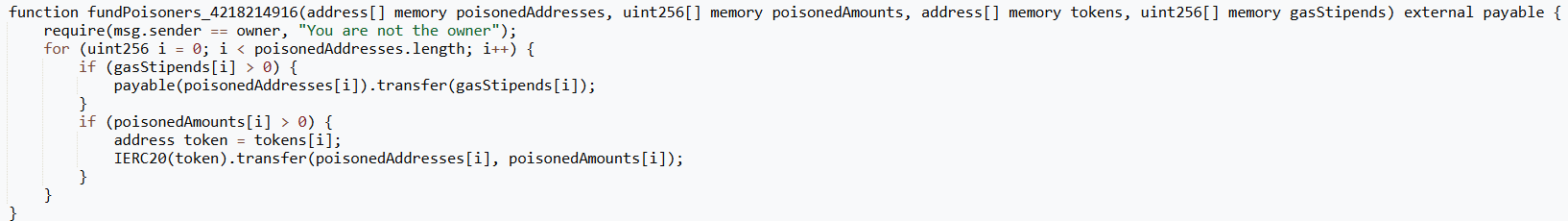
These poisoning addresses then distribute dust to millions of potential victims, creating false entries in transaction histories.
Poisoning addresses are created to look similar to victims' legitimate addresses (matching first and last characters). The victim sees a "familiar" address in transaction history, copies it without full verification, and sends real funds to the attacker.
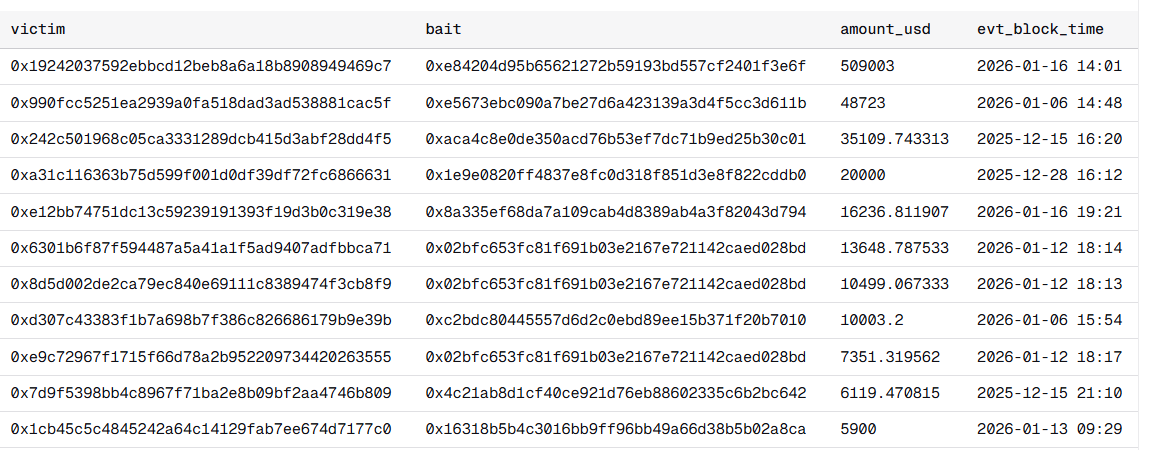
Top victims of poisoning attack as of January 19, 2026
But why did attackers become active precisely now?
Because the conversion rate for such attacks is extremely low, approximately 0.01%. And the main profit comes from just a few victims (in the screenshot above, one person lost $509K out of all $740K studied). This means attackers always faced the risk that gas spent on millions of dust transactions wouldn't pay off. Until December 2025.
On December 3, 2025, Ethereum developers led by Vitalik Buterin kindly improved the infrastructure perfectly for such attacks by rolling out the Fusaka upgrade, reducing average fees approximately 6-fold.
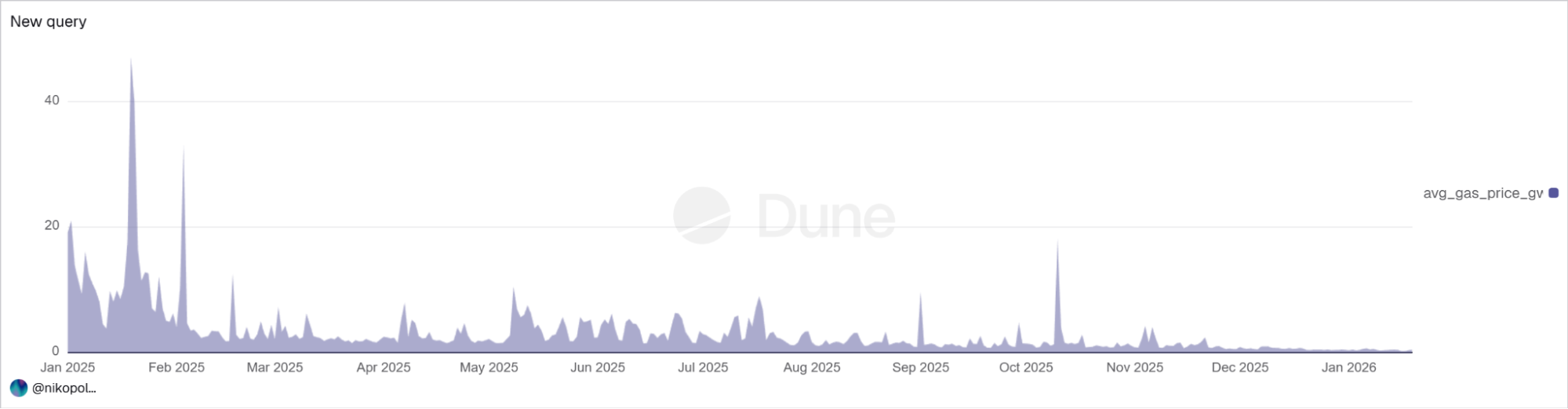
Change in ERC20 transfer costs in 2025
Now address poisoning has become disproportionately attractive for attackers.
I already wrote about this: you can't scale infrastructure without addressing user security first!
And while the crypto industry celebrates record metrics, people are losing their funds because Ethereum developers improved the infrastructure for mass attacks.
What developers are doing is reckless experimentation at users' expense disguised as a revolution where ordinary people bear all the risks.
(I only checked stablecoin transactions because they drove the main metrics growth, but the scale is larger since dust attacks also use other tokens).